With the route-target command for VRFs, the RT (Route Target) is added for all VPN routes. If you don’t want this, you can select which routes you want to import or export using a route-map. In the MPLS VPN VRF export map lesson, I explained how the export map works. This time we’ll take a look at the import map.
Let’s take a look at the following topology:
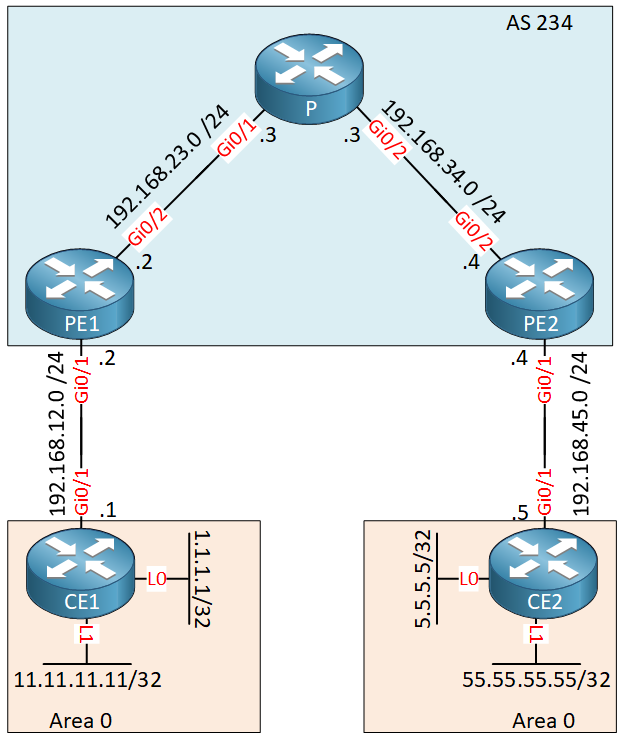
This is a standard MPLS VPN PE CE topology with a customer that uses OSPF on two sites. Each CE router has two loopback interfaces. Here is the VRF configuration from PE1 and PE2:
PE1#show running-config | begin ip vrf
ip vrf CUSTOMER
rd 1:1
route-target export 1:1
route-target import 2:2PE2#show running-config | begin ip vrf
ip vrf CUSTOMER
rd 1:1
route-target export 2:2
route-target import 1:1VPN routes on PE1 are exported with RT 1:1 and PE2 exports its VPN routes with RT 2:2.
With the route-target export command, all VPN routes are exported. There is no way to filter anything. This means that CE1 and CE2 will learn about each other’s routes that they advertise:
CE1#show ip route ospf
5.0.0.0/32 is subnetted, 1 subnets
O IA 5.5.5.5 [110/3] via 192.168.12.2, 00:02:26, GigabitEthernet0/1
55.0.0.0/32 is subnetted, 1 subnets
O IA 55.55.55.55 [110/3] via 192.168.12.2, 00:02:26, GigabitEthernet0/1
O IA 192.168.45.0/24 [110/2] via 192.168.12.2, 00:02:26, GigabitEthernet0/1CE2#show ip route ospf
1.0.0.0/32 is subnetted, 1 subnets
O IA 1.1.1.1 [110/3] via 192.168.45.4, 00:02:46, GigabitEthernet0/1
11.0.0.0/32 is subnetted, 1 subnets
O IA 11.11.11.11 [110/3] via 192.168.45.4, 00:02:46, GigabitEthernet0/1
O IA 192.168.12.0/24 [110/2] via 192.168.45.4, 00:02:46, GigabitEthernet0/1Let’s take a closer look at PE2, and see which VPN routes it has received from PE1:
PE2#show ip bgp vpnv4 all 1.1.1.1/32 | include Extended
Extended Community: RT:1:1 OSPF DOMAIN ID:0x0005:0x000000020200 PE2#show ip bgp vpnv4 all 11.11.11.11/32 | include Extended
Extended Community: RT:1:1 OSPF DOMAIN ID:0x0005:0x000000020200 PE2#show ip bgp vpnv4 all 192.168.12.0/24 | include Extended
Extended Community: RT:1:1 OSPF DOMAIN ID:0x0005:0x000000020200 These VPN routes are installed in the VRF of our customer:
PE2#show ip route vrf CUSTOMER bgp
1.0.0.0/32 is subnetted, 1 subnets
B 1.1.1.1 [200/2] via 2.2.2.2, 00:02:39
11.0.0.0/32 is subnetted, 1 subnets
B 11.11.11.11 [200/2] via 2.2.2.2, 00:00:26
B 192.168.12.0/24 [200/0] via 2.2.2.2, 00:00:26If you want to restrict the routes that PE2 installs in the VRF then you could use an export-map on PE1. However, what if I want to control this from PE2?
That’s when the import map becomes useful…
Configuration
I’ll use the topology that I just showed you.
- Configurations
- CE1
- CE2
- P
- PE1
- PE2
Want to take a look for yourself? Here you will find the startup configuration of each device.
Let’s configure PE2 so that CE2 only learns 1.1.1.1/32. The other two routes should be filtered.
I can do this with a prefix-list and a route-map:
PE2(config)#ip prefix-list CE1_L0 permit 1.1.1.1/32
PE2(config)#route-map IMPORT_MAP permit 10
PE2(config-route-map)#match ip address prefix-list CE1_L0The route-map has a single permit and only matches 1.1.1.1/32. Let’s activate it:
PE2(config)#ip vrf CUSTOMER
PE2(config-vrf)#import map IMPORT_MAPLet’s see how this influences PE2:
PE2#show ip bgp vpnv4 all 1.1.1.1/32 | include Extended
Extended Community: RT:1:1 OSPF DOMAIN ID:0x0005:0x000000020200 PE2#show ip bgp vpnv4 all 11.11.11.11/32 | include Extended
Extended Community: RT:1:1 OSPF DOMAIN ID:0x0005:0x000000020200 PE2#show ip bgp vpnv4 all 192.168.12.0/24 | include Extended
Extended Community: RT:1:1 OSPF DOMAIN ID:0x0005:0x000000020200 The VPN routes are still there…nothing changes. However, what does change is the routing table for our VRF:
- Unit 1: Introduction
- Unit 2: LDP (Label Distribution Protocol)
- Unit 3: MPLS VPN
- VRFs (Virtual Routing and Forwarding)
- MPLS L3 VPN Explained
- MPLS L3 VPN Configuration
- MPLS L3 VPN BGP Allow AS in
- MPLS L3 VPN BGP AS Override
- MPLS L3 VPN PE-CE RIP
- MPLS L3 VPN PE-CE EIGRP
- MPLS L3 VPN PE-CE OSPF
- MPLS L3 VPN PE-CE OSPF Default Route
- MPLS L3 VPN PE-CE OSPF Global Default Route
- MPLS L3 VPN PE-CE OSPF Sham Link
- VRF Lite Route Leaking
- MPLS VPN Extranet Route Leaking
- MPLS VPN VRF Export Map
- MPLS VPN VRF Import Map
- MPLS over FlexVPN
- Unit 4: MPLS L2 Encapsulation
- Unit 5: IPv6 MPLS
- Unit 6: MPLS Traffic Engineering (TE)
- Introduction to MPLS Traffic Engineering (TE)
- MPLS Traffic Engineering (TE) IS-IS Configuration
- MPLS Traffic Engineering (TE) OSPF Configuration
- MPLS TE RSVP-TE
- MPLS TE Static Routes
- MPLS TE Policy Based Routing (PBR)
- MPLS TE Autoroute Announce
- MPLS TE Autoroute Destination
- MPLS TE Autoroute Metric
- MPLS TE Unequal Cost Load Balancing
- MPLS TE Load Balancing between IGP and TE
- MPLS TE Forwarding Adjacency
- MPLS TE Path Options Explicit
- MPLS TE Class-Based Tunnel Selection (CBTS)
- MPLS TE Metric
- MPLS TE Setup and Hold Priority
- MPLS TE Attribute Flag and Affinity
- MPLS TE Reoptimization
- MPLS TE Fast Reroute (FRR)
- MPLS TE Fast Reroute Path Link Protection
- MPLS TE Fast Reroute Path Node Protection
- MPLS TE FRR RSVP Hello Support
- MPLS TE DiffServ Aware (DS-TE) Traditional
- MPLS TE Diffserv-Aware (DS-TE) IETF Mode
- MPLS VPN over MPLS TE Tunnels
- MPLS TE Per VRF TE tunnel