OSPF TTL Security Check
The OSPF TTL security check is a mechanism that protects OSPF against remote attacks. When you enable this feature, OSPF will send packets with a TTL of 255 and rejects any packets with a TTL that are smaller than a configured threshold. By default, once you enable this it will only accept packets with a TTL of 255. Since routing decrements the TTL by one, this means that only OSPF packets from directly connected devices will be accepted.
Let’s look at an example. I will use the following topology:
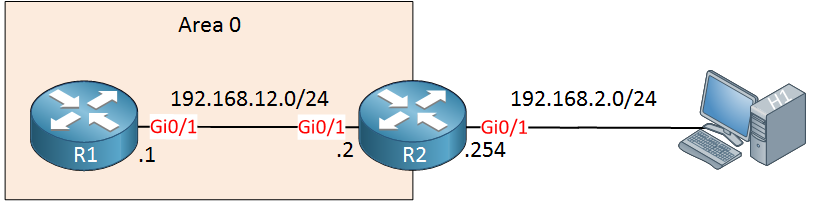
Above we have two routers running OSPF, behind R2 is an attacker that wants to attack R1. It will do so by sending spoofed unicast OSPF packets destined to 192.168.12.1:
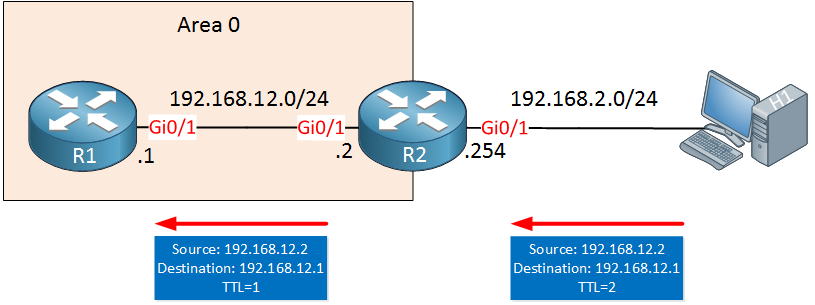
H1 sends a spoofed OSPF, impersonating R2 and destined to R1. When R2 forwards this packet, the TTL will be decreased by 1 and R1 will receive the IP packet. Even if OSPF rejects the packet because the content is garbage, it still has to be processed by the control plane. If H1 sends enough packets, it might succeed in overloading the router’s control plane.
To stop a remote attack like this, we can implement the OSPF TTL security check.
By default, all OSPF packets have a TTL of 1 as you can see in the packet capture below:
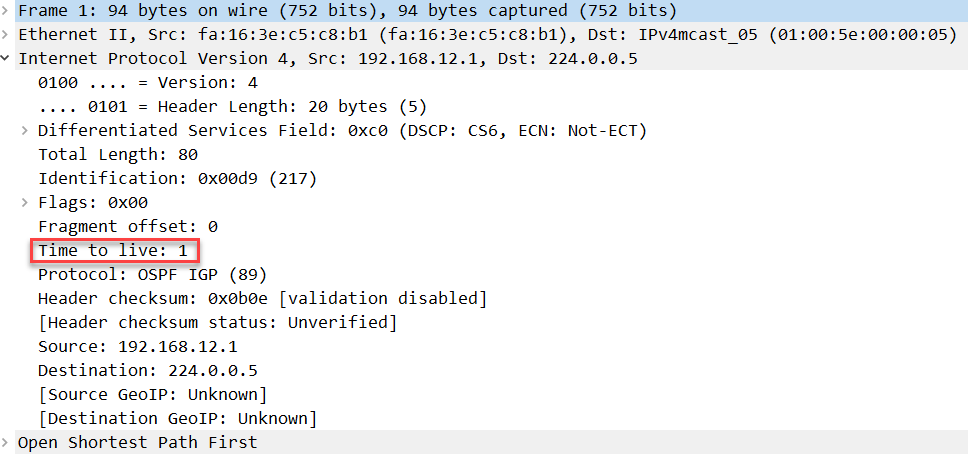
When TTL security check is enabled, OSPF will only accept packets with a certain TTL value, 255 by default. When it receives packets with a lower TTL, they will be discarded.
Configuration
Let’s give this a try. We can enable this globally for all interfaces like this:
R1(config)#router ospf 1
R1(config-router)#ttl-security all-interfacesYou can also enable TTL security check on the interface level with the ip ospf ttl-security command.
As soon as you enable this on one router, the neighbor adjacency with R2 will drop once the dead timer expires. Why? We can see the reason when we enable a debug:
R1#debug ip ospf adj
OSPF adjacency debugging is onOn the console of R1, you will see this message:
R1#
OSPF-1 ADJ Gi0/1: Drop packet from 192.168.12.2 with TTL: 1R1 will now only accept packets with a TTL of 255 and since R2 is sending OSPF packets with a TTL of 1, they are discarded. Let’s enable TTL security on R2 as well:
R2(config)#router ospf 1
R2(config-router)#ttl-security all-interfacesThe OSPF neighbor adjacency will recover and both R1 and R2 are now sending OSPF packets with a TTL of 255 to each other:
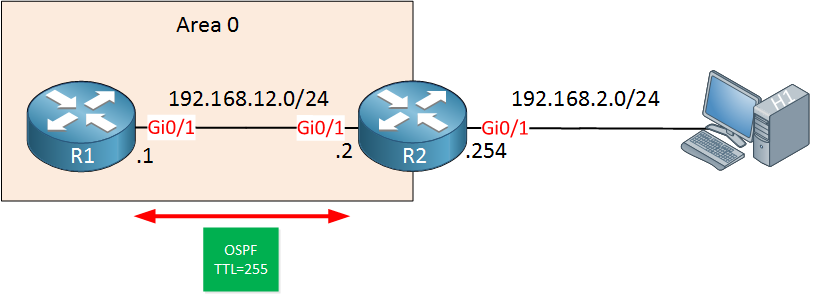
Here’s a packet capture where you can see the new TTL value:
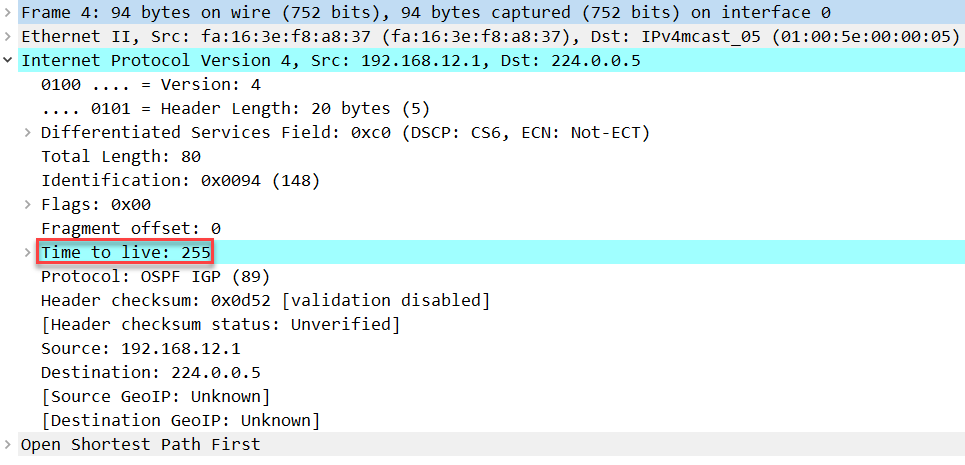
Wireshark Capture OSPF TTL Security Check
Above you can see that the TTL is now 255. Since this is the highest value possible for the TTL field, it is impossible for H1 to send a spoofed unicast OSPF packet to R1, preventing a remote attack like this.
The TTL security check is not applied to virtual links or sham links by default. If you want to use this, then you can use the area virtual-link ttl-security or area sham-link ttl-security commands.
By default, the lowest TTL that OSPF TTL security check will accept is 255. You can add the hops parameter to use another value. For example, if you use ttl-security all-interfaces hops 100 then OSPF will accept all OSPF packets with a TTL of 155-255.
That’s all there is to it. You can read more about TTL security in the following RFC: The Generalized TTL Security Mechanism (GTSM)
Unit 1: Introduction to OSPF
- Introduction to OSPF
- Basic OSPF Configuration
- OSPF Multi Area Configuration
- OSPF Reference Bandwidth
- OSPF Plain Text Authentication
- OSPF MD5 Authentication
- OSPF SHA-HMAC Authentication
- OSPF TTL Security Check
- OSPF Default Route
Unit 2: OSPF Neighbor Adjacency
- OSPF LSA Types
- OSPF LSAs and LSDB Flooding
- OSPF Hello and Dead Interval
- OSPF Router ID
- OSPF Packets and Neighbor Discovery
- OSPF DR/BDR Election
- OSPF Passive Interface
- Troubleshooting OSPF Neighbor Adjacency
Unit 3: OSPF Network Types
- OSPF Non-Broadcast Network Type
- OSPF Broadcast Network Type
- OSPF Point-to-Multipoint Network Type
- OSPF Point-to-Multipoint Non-Broadcast Network Type
- OSPF Point-to-Point Network Type
- OSPF Next Hop with Network Types
Unit 4: OSPF Stub Areas
- Introduction to OSPF Stub Areas
- How to configure OSPF Stub Area
- How to configure OSPF Totally Stub
- How to configure OSPF NSSA (Not So Stubby) Area
- How to configure OSPF Totally NSSA (Not So Stubby) Area
- OSPF NSSA P-bit explained
Unit 5: Advanced OSPF Topics
- OSPF Summarization
- OSPF Distribute-List Filtering
- OSPF LSA Type 3 Filtering
- OSPF LSA Type 5 Filtering
- OSPF Virtual Link
- OSPF Virtual Link Authentication
- OSPF Path Selection Explained
- How to read the OSPF Database
- OSPFv3 for IPv4
- Troubleshooting OSPF Route Advertisement
- OSPF SPF Scheduling and Throttling
- OSPF LSA Throttling
- OSPF Incremental SPF
- OSPF Prefix Suppression
- OSPF Stub Router
- OSPF Graceful Shutdown
- OSPF Graceful Restart
- OSPF Loop-Free Alternate (LFA) Fast Reroute (FRR)
- OSPF Remote Loop-Free Alternate (LFA) Fast Reroute (FRR)