Ques 1. What are iRules in F5 LTM?
iRule is code that will influence network traffic in a variety of ways. iRule allows the F5 to manipulate and perform event driven functions to the application traffic as it passes through the F5 LTM.iRule can perform functions like route, re-route, redirect, inspect, modify, delay, discard or reject and log. It can further perform plethora of functions to be done on traversing traffic.
Ques 2. What is iControl?
iControl is an open, web services based API that allows complete, dynamic, programmatic control of F5 configuration objects. This means we can add, modify or remove bits from F5 device automatically. iControl uses SOAP/XML to ensure open communications between systems.

Ques 3. What is the default LTM MGMT port IP Address?
192.168.1.245
Ques 4. What is ConfigSync?
Config sync is short for Configuration synchronization. It is a process where we replicate/propagates one unit main config file on the peer unit in a device group.
Ques 5. What is OneConnect and its benefit?
“OneConnect” is trademark feature of F5 LTM (Local Traffic Manager) which uses the concept of Connection Reuse Pool i.e. after LTM has sent request and received full response through the connection, these connections are not torn down, rather put in the Connection reuse Pool. When a new Client creates TCP connection with LTM, LTM reuses existing TCP connection from Connection Reuse Pool instead of creating new LTM-Server TCP connection. This approach saves the system resources like memory, CPU processes etc. of LTM and Server.

Ques 6. What is a load balancing pool?
A load balancing pool contains group of devices (like web servers) to receive and process traffic. The request initiated from Client is intercepted by BIG-IP LTM which further sends the request to any of the member’s part of load balancing pool. This helps to efficiently distribute the load on server resources.
Ques 7. What is meaning of session persistence and why is it required?
Persistence is also called stickiness – It’s a technique implemented by LTM to ensure requests from a single user are always sent to the server on which they started. A very good and practical example of session persistence is when shoppers are buying something online which requires the customer to maintain persistence to a single server during the lifetime of the session.
The 2 key types of session persistence are –
- Cookie
- Source IP
The load balancer would insert a cookie to uniquely identify the session the first time a client accessed the site and then refer to that cookie in subsequent requests to persist the connection to the appropriate server.
In case Source IP Address based persistence, LTM directs traffic to the same server based upon the clients source IP address. However, we have a catch here – When original Client Source IP is traversing via a NAT or proxy device, in which all connections appear to originate from a single IP.
Other known Persistence techniques are –
- Destination address affinity persistence
- Hash persistence
- SIP persistence
- SSL persistence
- Universal persistence
- Microsoft Remote Desktop Protocol persistence
Ques 8. What is a profile?
Profile is used to control the behaviour of network traffic for application delivery. Simply put, a profile is a group of settings, with values, that corresponds to a specific type of traffic like HTTP or FTP traffic. Infact, BIG-IP uses profiles to manage how we want to manage that traffic type. After configuring a profile, we need to associate the profile with a virtual server. The virtual server then processes traffic according to the values specified in the profile.
Ques 9. What is RAM cache?
RAM Cache is a feature to serve content to clients directly from the memory of your F5 appliance. RAM cache performs cache of HTTP objects stored in the BIG-IP system’s RAM that are reused by subsequent client request. As shown in below example, Client “A” request for ABC.gif content is provided by the Server. Next request for same content i.e. ABC.gif is locally provided by the BIG-IP box via RAM Cache instead of sending request to Server which is pool member.

The benefits which can be reaped from RAM cache are –
- Significant reduction of server load
- Improvement of user experience speed with content provided in RAM Application technology
- Reduction of server load
- Reduced latency
Ques 10. What type items are cached and not cached by RAM feature?
RAM Cache feature can perform caching of following content types –
- 200, 203, 206, 300, 301, and 410 responses
- Responses to GET methods, by default
- Other HTTP methods for URIs specified for inclusion in cached content/ iRule
- Content based on the User-Agent and Accept-Encoding values.
Items that RAM cache does not cache are –
- Private data specified by cache control headers
- HEAD, PUT, DELETE, TRACE, and CONNECT methods.
Ques 11. What type of lists are considered in URI Lists for including/excluding from caching?
What is their order of preference?
There are 3 URIs F5 system may use –
Pin List– Lists the URIs for responses that you want the system to store indefinitely in the RAM cache.
Include List – Lists the URIs that are typically ineligible for caching, but the system caches them. When you add URIs to the Include List, the system caches the GET methods and other methods, including non-HTTP methods.
Exclude List – Lists the URIs that are typically eligible for caching, but the system does not cache them.
Following order of preference, in decreasing order –
- Exclude List
- Pin List
- Include List
Ques 12. Difference between Node and Pool member?
Node and pool member are 2 terms used commonly in F5 LTM setup. The difference between a node and a pool member is that a node is designated by the device’s IP address for e.g. – 192.168.10.10, while pool member includes an IP address and a service for e.g. – 92.168.10.10:80.Another key difference between 2 terms is that while health monitor for node is used to report status of device itself, a health monitor for a pool member reports the status of a service running on the device.
Ques 13. What are Virtual Servers?
Clients on an external network can send application traffic to a Virtual Server, which then directs the traffic to the actual servers. For the client the pool of the servers is a single server called virtual server. The primary purpose of a virtual server is to load balance traffic across a pool of servers on an internal network. Virtual servers increase the availability of resources for processing client requests.
In below example, the client sends request to Virtual Server IP address which it translates to available real Sever IP for completing the communication between Client and actual server.

Note – In many deployments, there may be need to change Source IP of Client using SNAT which is not used in this case.
Ques 14. What are types of pools on the F5 system?
- types of pools can be configured on F5 system –
- Server Pools – Pool containing one or more server nodes that process application traffic. Web Servers is closest example of Server Pools.
- Gateway Pools – A Pool of Routers is called Gateway Pool.
- Clone Pools – When it is required to send traffic to pool of Intrusion Detection Systems (IDSs), Clone pool is configured.
Ques 15. What is meant by member?
A Pool Member is a logical object that represents a physical node on the network. Once you have assigned a pool to a virtual server, the BIG-IP system directs traffic coming into the virtual server to a member of that pool. An individual pool member can belong to one or multiple pools, depending on how you want to manage your network traffic. Pool member includes an IP address and a service for e.g. – 192.168.10.10:80.
Ques 16. What is TMM and its functionality?
TMM is abbreviation for Traffic Management Microkernel. It is basically the brain of BIGIP.TMM handles all of BIG-IP’s local traffic functionality such as –
- Intelligent load balancing
- Compression
- SSL
- iRules
- Packet filters etc.
(With the exception of L4-only load balancing). TMM is also responsible for delivering traffic to the Host Management subsystem .TMM is the core component of TMOS as it handles all network activities and communicates directly with the network switch hardware.
Ques 17. What is key difference between LTM and GTM?
Below table enumerates difference between GTM and LTM-

Ques 18. What is a tagged Interface?
Tagged interfaces in F5 terminology is similar to Trunk interfaces on Cisco devices. When we want to assign a single interface to multiple VLANs “Tagged” Interfaces need to be configured. A tagged interface is an interface that you assign to a VLAN in a way that causes the system to add a VLAN tag into the header of any frame passing through that interface.
Below is one example Where Tagged interface on BIG-IP traverses 3 VLANs (A, B and C) –

Ques 19. Which Command line utility displays real-time statistical information for BIG-IP LTM?
Bigtop is the command which displays real-time statistical information.
Following items are displayed when using the Bigtop utility:
- Current time
- Network activity in bits, bytes, packets, or requests
- Nodes available for virtual servers
- Current state of nodes
Ques 20. What is cookie persistence?
Cookie persistence is a mode of persistence where the BIG-IP system stores Persistent connection information in a cookie.
Ques 21. What is Self IP address?
“Self IP” term is associated with VLAN for each device. Each BIG-IP has a self-IP in a VLAN which is the IP defined on the interface. Self IP is similar to SVI in Cisco where we assign IP Address to VLAN.
Self IP Address in F5 LTM is used mainly for below 3 purpose –
- F5 compares destination server IP address with VLAN self IP address to identify which VLAN it belongs to. Also, It is the source address when Automap SNATting.
- Self IP Address can also be used as the Default gateway for systems on an internal VLAN.
- Self IP Address is also used to send monitor probes to the group of servers in that VLAN.
Ques 22. What is floating self IP address?
A Floating self IP address is an additional self IP address for a VLAN that serves as a shared address by both units of a BIG-IP redundant system. Floating Self IP is like HSRP virtual IP. It will float to active unit when failover occurs.

Ques 23. What is HTTP chunking?
HTTP chunking refers to the HTTP/ 1.1 feature known as chunked encoding, which allows HTTP messages to be broken up into several parts. Chunking is most often used by servers when sending responses.
Ques 24. Which are the latest ADC (includes LTM) hardware models in market?
Few of LTM (Viprion ADC) hardware models active in Load balancer market are –
- VIPRION 4800 Chassis
- VIPRION 4480 Chassis
- VIPRION 4450 Blade
- VIPRION 4340N/4300 Blade
- VIPRION 2400 Chassis
- VIPRION 2200 Chassis
- VIPRION 2250 Blade
- VIPRION 2150 Blade
Ques 25. What is pipelining?
Pipelining is a feature of HTTP/1.1 that allows clients to make requests even when prior requests have not yet received a response from the server.
Ques 26. What is Predictive method?
Predictive method is a dynamic load balancing method that performs connection distribution on a combination of two factors –
- Server that currently hosts the fewest connections
- Server having the fastest response time.
Predictive method also ranks server performance over time, and passes connections to servers which exhibit an improvement in performance.
Ques 27. What are the capabilities of LTM? Below are the key capabilities/functions of LTM –
- Traffic Load Balancing to distribute server load and achieve scalability.
- Health monitoring and server performance for availability.
- Leveraging OneConnect utility to aggregate multiple client requests into a server-side connection pool hence improving performance.
- Off-loading server of HTTP data compression, SSL authentication, and SSL encryption to improve server performance.
- Achieving connection persistence.
- Managing authentication, authorization and SSL certificate credentials.
- Optimizing performance for specific types of connections.
Ques 28. Which tasks are performed by LTM to offload server of resources?
The tasks that the BIG-IP system can offload from a network server are –
- SSL certificate-based authentication and authorization
- SSL encryption and decryption
- HTTP data compression and RAM caching
- Authentication and authorization of application traffic using LDAP / RADIUS servers
- The rewriting of Microsoft Remote Desktop connections
Ques 29. What are the authentication modules that can be implemented on F5 Big-IP?
The authentication modules that the BIG-IP system provides are as follows –
- An LDAP module
- A RADIUS module
- A TACACS+ module
- An SSL Client Certificate LDAP module
- An SSL OCSP (Online Certificate Status Protocol) module
Ques 30. What is difference between APM and PAM?
PAM is Abbreviation for Pluggable Authentication Module technology while APM is short for Access Policy Manager. While PAM is used by Big-IP to authenticate Administrators on Linux system, APM is used to authenticate or authorize users to access to your applications.
Ques 31. What are the load balancing methods used in LTM?
Following are load balancing options available in F5 LTM –
- Round Robin
- Ratio (member) and Ratio (node)
- Dynamic Ratio (member) and Dynamic Ratio (node)
- Fastest (node) and Fastest (application)
- Least Connections (member) and Least Connections (node)
- Observed (member) and Observed (node)
- Predictive (member) and Predictive (node)
Ques 32. Which all Health monitors are available on F5 LTM?
There 4 main types of monitoring are –
- Address Check – This is simplest of all checks and uses ICMP protocol to verify reachability to IP address and marks the node down when no response is received to ICMP request.
- Service Check – Refers to monitoring the port of IP address. Working at Layer 4, the request is sent to port number of destination to verify up/down status.
- Content Check – This monitor goes upto level of verifying the correctness of content server is delivering. A command is sent for e.g. HTTP GET request and response is examined for received string.
- Interactive Check – In such type of monitors, a TCP connection that is opened, commands are then sent and corresponding responses are examined. The member up/down status is validated based on fail/success criteria.
Ques 33. What are the deployment modes of F5 LTM?
F5 LTM can be deployed in 3 types of modes –
- 1-Arm deployment
- 2-Arm deployment
- In-Path/DSR (Direct Server Return) deployment
One Arm Deployment

The Virtual IP of F5 will be on same subnet as nodes. Basically the F5 and Nodes are connected to same broadcast domain or same Vlan. Further SNAT (Source NAT or Secure NAT) is configured on F5 to convert the Source IP of remote Client to its Self IP.
Two Arm Deployment
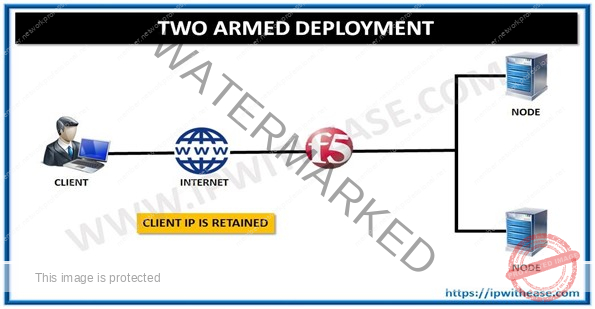
DSR Deployment

It is just like One-Arm deployment .In this scenario, the term Direct server return holds true – The forward oath from Client goes to F5 and F5 forwards the request further towards respective Node , however what chanbges is the return path .The return path from Node (when responding to client request via F5 ) directly goes towards the Client and does not traverse via F5 LTM.The entire feature set of Server Load balancer can be achieved while other supporting features are not possibke in such type of deployment.
Ques 34. What is SNAT in F5 LTM?
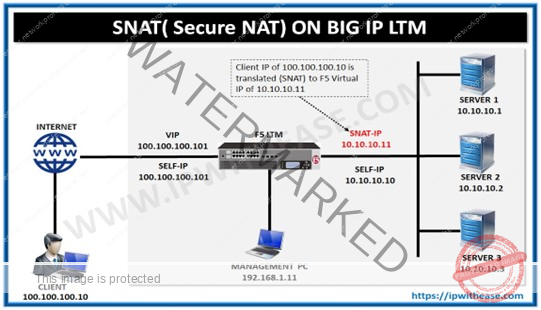
SNAT is abbreviation for Secure Network Address Translation. SNAT maps the source client IP address in a request to a translation address defined on the BIG-IP device. When the BIG-IP system receives a request from a client, and if the client IP address in the request is defined in the origin
address list for the SNAT, the BIG-IP system translates the source IP address of the incoming packet to the SNAT address.
Ques 35. How does SNAT work?

SNAT works in the following way –
- The LTM system receives a packet from an original client IP address and checks to see if that source address is defined in a SNAT.
- If the client’s IP address is in SNAT, LTM changes that source IP address to the translation address defined in the SNAT.
- LTM sends the client request, with the SNAT translation address as the source address, to the target server.
Ques 36. What is rate shaping?
Rate Shaping is a feature of BIG-IP LTM which allows us to categorize certain types of connections into rate classes, for the purpose of customizing the throughput of those connections. This approach is especially useful when you want to optimize Business Critical traffic like web-server traffic over less critical Internet based traffic. In layman terms, Rate shaping controls bandwidth consumption, using rate classes that are customizable.
Ques 37. What are 3 key elements of iRule?
The 3 basic elements of iRules are –
- Event declarations
- Operators
- iRule commands
Ques 38. What is the minimal RAM required to run BIG-IP Virtual Edition on ESXi?
4 GB
Ques 39. What are key elements to be considered while selecting an F5 Load balancer (LTM/ADC)?
Selecting an LTM/ADC of BIG-IP Appliances primarily depends on needs of the customer. Following are the key items –
- Connections per second (L4/L7)
- SSL Traffic (SSL TPS)
- Number and type of Network ports
- Throughput of LTM
The above considerations should take into account future growth of users/application traffic for atleast 5 years ahead.
Ques 40. What is full proxy architecture in F5?

Full proxy Architecture uses the methodology to have two separate entities with two separate session tables i.e. one on the client-side and another for the server-side. The BIG-IP LTM device manages the two sessions independently. The connections between the “Client to LTM” and “LTM to Server” are independent of each other.
We can render following key benefits from Full proxy architecture –
- Clients often experience higher latency due lower bandwidth connections while the server’s side are low latency due to high-speed LAN. The optimizations and acceleration techniques on both client side and Server Side are different. Since both sides of connections are managed separately, therefore simultaneous optimization of Client and Server side becomes possible in Full Proxy.
- Another key benefit is that since in full proxy connections traverse through the device, therefore SSL termination, enforcement of security policies, and performance-related services can be implemented on a per-client and/or per-application basis.