50 Cloud Engineer Interview Questions and Answers
Q1. What is cloud?
Cloud refers to servers which are accessible over the Internet and software and databases run on them.
Q2. Differentiate between cloud and cloud computing?
Cloud terminology refers to servers hosted on the Internet where services related to software, databases run on them. Cloud computing refers to computing infrastructure which is available on demand related to servers, storage, databases, software, analytics and intelligence.
Q3. What are various cloud service models? Explain in brief
-
IaaS – Infrastructure as a service in which provider rents hardware and infrastructure as service to enterprise such as memory, computing, servers etc.
-
SaaS – Software as a service in which provider software resides as a service on cloud. Software and applications are used on subscription models. Cloud provider is responsible for maintenance and upgrade of application / software and application communication happens over API.
-
PaaS – Platform as a service provider provides a platform where enterprises can deploy their code and applications. PaaS packages comprises of data, storage, and computing capability for development and testing
Q4. What are the different deployment models in cloud environment?
Cloud offers four deployment models namely public cloud which is free for use such as Internet, Private cloud which is collection of resources which a private organization employees use Community clouds allow multiple organizations to access services and systems to share information and computing, Hybrid cloud is a mix of private and public clouds such as on premises infrastructure and public cloud such as Amazon AWS, Google cloud etc.
Q5. Who coined the term ‘Cloud computing’?
‘Cloud computing’ term was coined by Google CEO Eric Schmidt in year 2006
Q6. What is edge computing?
Terminology related to distributed processing architecture in which client data is processed as close to its originating source as possible
Q7. Differentiate between scalability and elasticity with reference to cloud computing?
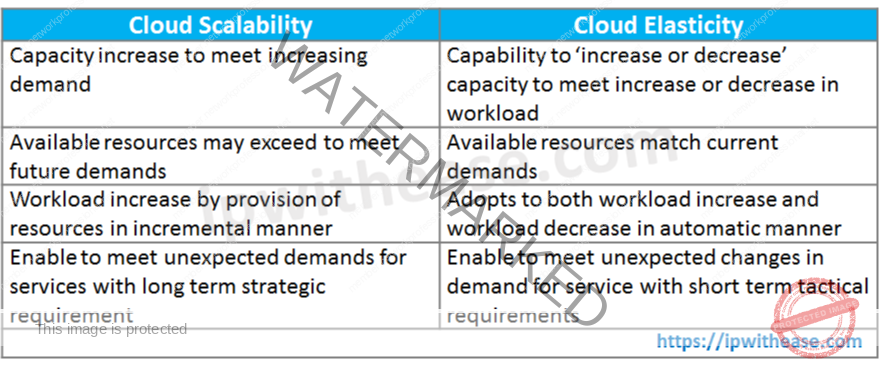
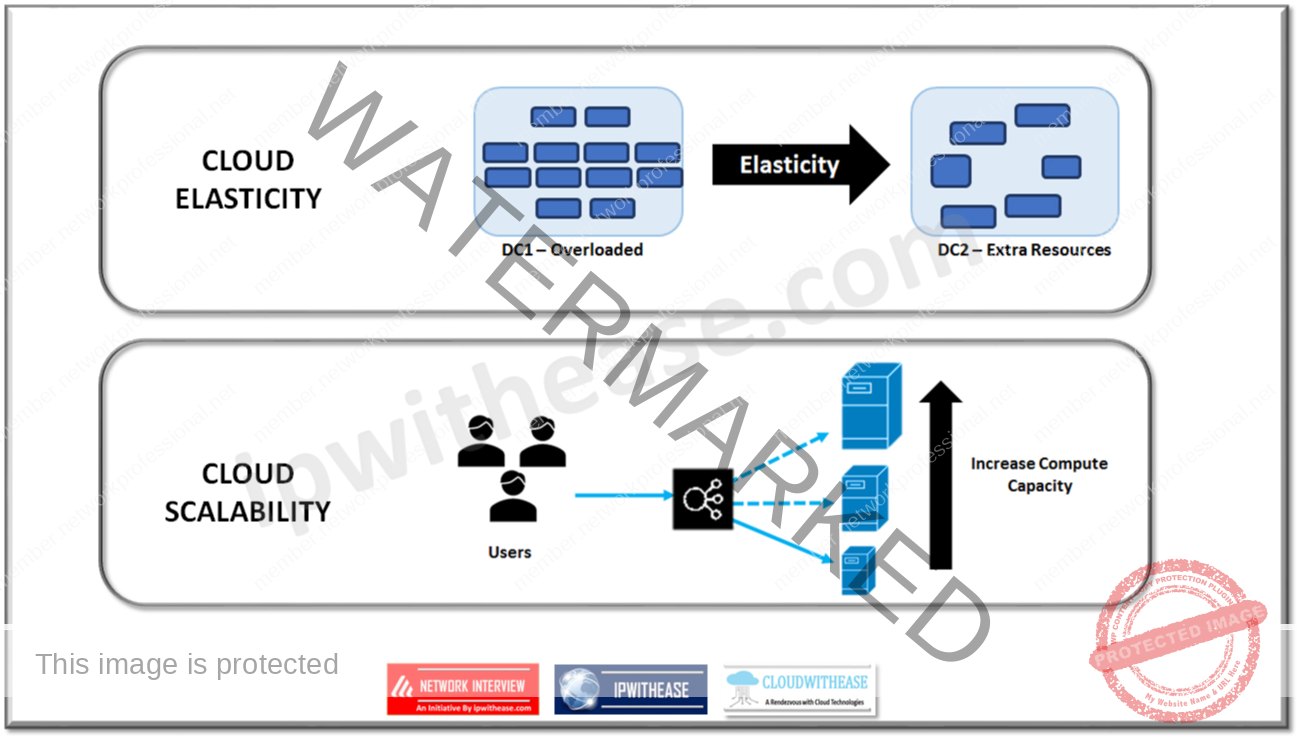
Q8. Explain reliability and availability in the context of cloud computing.
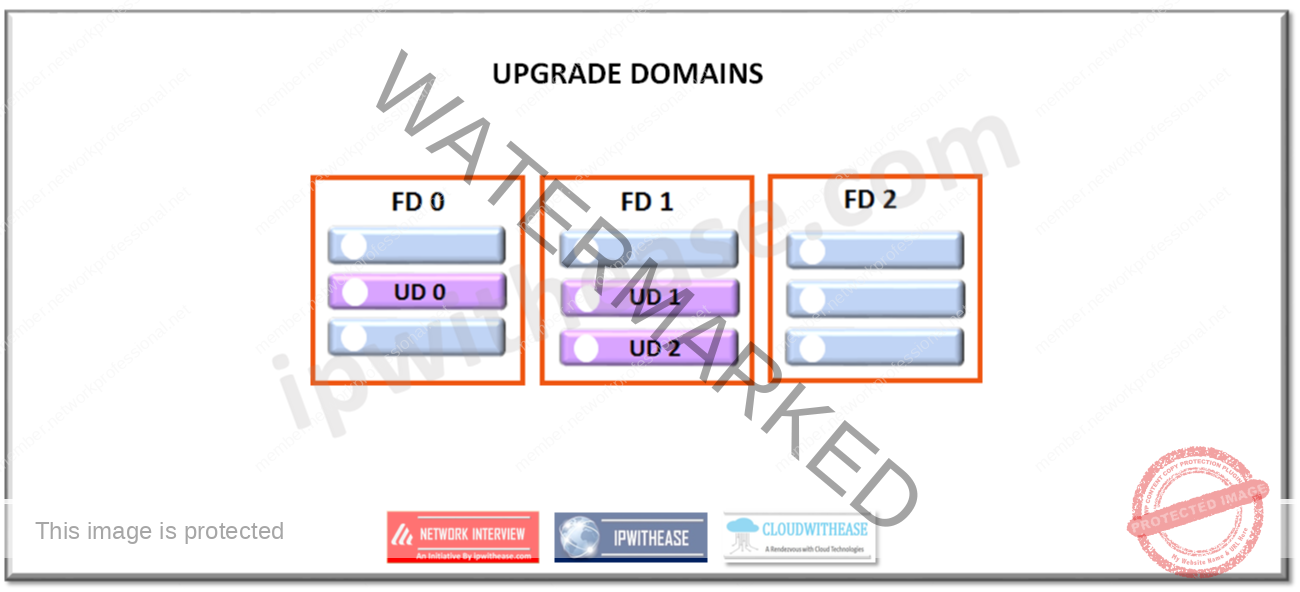
Use of fault domains and upgrade domains in cloud computing helps to achieve reliability and availability. When two virtual machines are in a single fault domain single hardware failure can bring down both virtual machines , automatic distribution of instances of roles across fault domains ensure availability.

Use of upgrade domains is beneficial to ensure availability as when a new version of software is rolled out, only one up gradation of domain is done at a time to ensure any instance of service is available always and availability of applications across multiple instances.
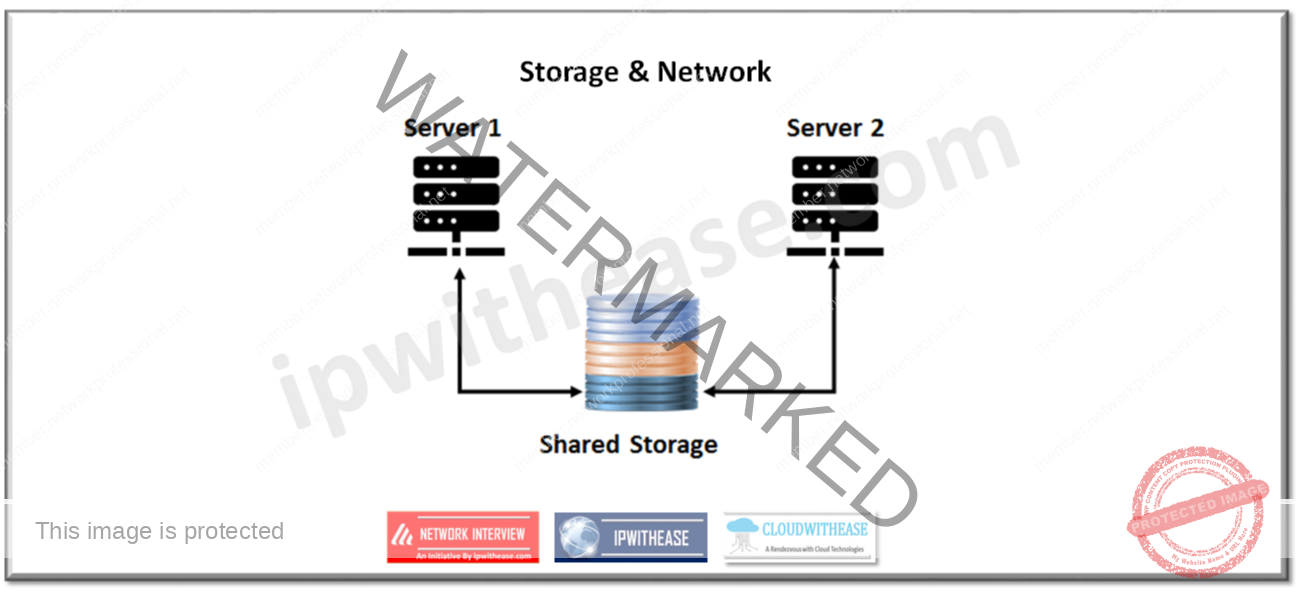
Storage and network availability is achieved by keeping copies of data in different domains to guard against DoS and DDoS attacks.
Q9. Explain different types of cloud storage levels.
Cloud offers object, block and file level storage.
Object storage – is a form of data storage architecture which stores large amounts of unstructured data. It designates each piece of data as an object, keeps it in a separate storehouse and bundles with metadata with a unique identifier for ease of access and retrieval.
Block storage – is used for structured data and uses blocks which are a set sequence of bytes to store structured workloads. Each block is assigned a unique hash value which functions as an address. The data is stored without any metadata e.g. data format, type, ownership etc. Ideal for databases and applications.
File storage – commonly used for unstructured data, it stores data in hierarchical architecture; as such that data and its Meta data is stored as in the form of files and folders.
Q10. Define the term ‘Multi-cloud’
Multi-cloud refers to multiple public clouds. Companies may use multi-cloud deployments instead of relying on one single cloud provider objective is redundancy and system backups. It helps to reduce risk of vendor lock in and free to pick and choose most affordable services from different vendors.
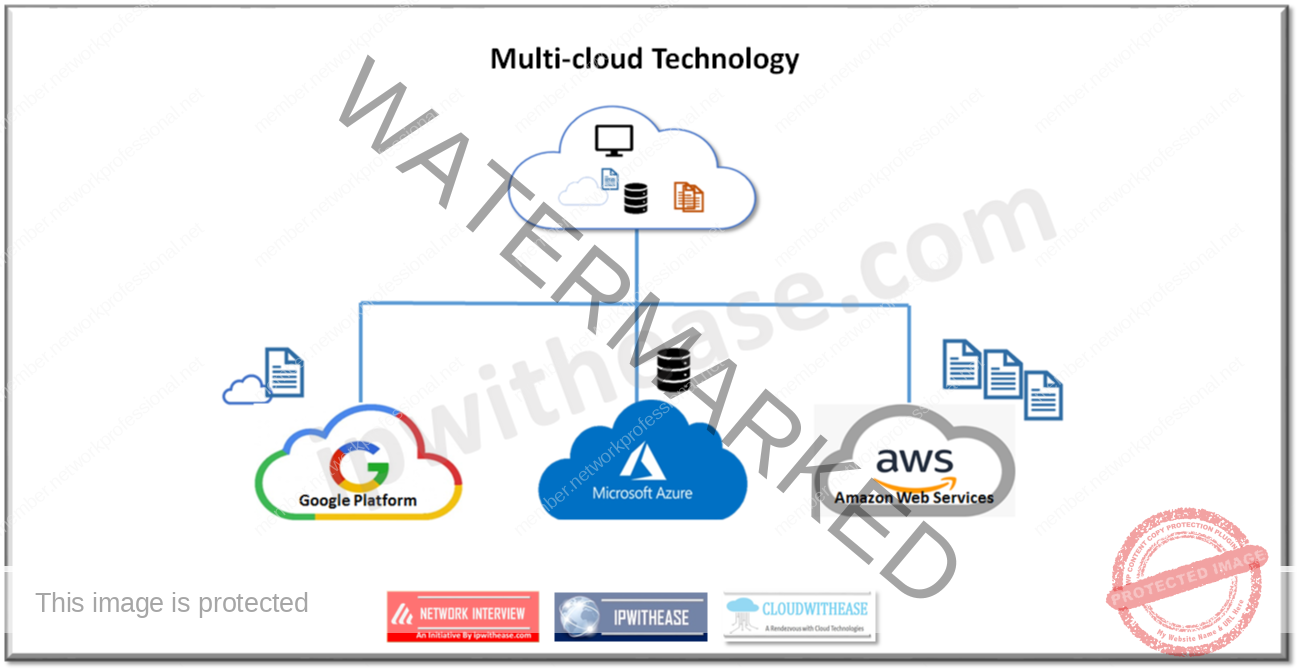
Q11. Explain the term ‘Shadow IT’.
‘Shadow IT’ is the usage of information technology systems, devices, software, applications and services without explicit approval from IT department. Users can go ahead and download apps and services from cloud without the knowledge of IT or security groups. Such applications represent a security gap.
Q12. What is a cloud firewall?
A cloud firewall is a security product like a traditional firewall which filters malicious traffic on a network. Cloud firewalls are hosted on cloud and this is also referred to as Firewall as a service (FWaaS). Cloud based firewalls form a virtual barrier around cloud platform, infrastructure and applications and they can also protect on premises infrastructure.

Q13. What are some popular examples of shadown IT applications?
Dropbox, Google Docs, Slack, Skype, Excel Macros etc.
Q14. Have you heard of the term ‘Eucalytus’? Elaborate.
Eucalytus is an Elastic utility computing architecture linking programs to useful systems. It is an open source Linux based software architecture for implementing cloud functionality at IaaS level. It is specially designed for ease of installation and maintenance in research settings, and easy to modify, instrument and extend. It can be deployed or executed without modification in underlying infrastructure. It supports secure communication.
Q15. Differentiate between Hybrid cloud and Hybrid IT.
Hybrid cloud refers to the combination of public and private clouds bound together by technology. Hybrid clouds give more agility to business, more flexibility, more deployment options, and help in minimizing costs, and optimizing existing infrastructure, security and compliance.
Legacy systems present in in house data centers which cannot be always migrated to cloud without a complete overhaul of technical and financial landscape. Organizations can mix traditional IT systems and adopt a variety of cloud deployments and both systems can be managed collectively such systems are referred as hybrid IT.
Q16. Compare Public, Private and Hybrid cloud computing types.

Q17. Explain the functioning of various layers in cloud architecture.
Cloud architecture comprises of: Storage controller, Node controller, cloud controller, Walrus and cluster controller
-
Storage controller – provides storage area in block form which can be dynamically attached by virtual machine.
-
Node controller – provides the functionality of a hypervisor that controls the VM activities, which includes execution, management and termination of many instances
-
Cloud controller – is used to manage virtualized resources like servers, storage, network with user APIs
-
Walrus – is used for the storage and acts as a storage controller to manage user demands. It has a scalable approach to control the virtual machine images and user data
-
Cluster controller – is used to control all virtual machines for executions the virtual machines are stored on the nodes and manages the virtual networking between virtual machines and external users.
-

Q18. What are the different types of data centers in cloud computing?
Cloud computing offers different types of data centers linked to grid architecture. The main types are containerized data center and low density data center. Containerized data centers provide a high level of customization. Customers can choose the different types of servers, memory, network and other infrastructure resources. Also the provider has to plan temperature control, network management and power management in these data centers. In Low density data centers we get a high level of performance by optimizing the number of servers in the data center.
Q19. Explain role of API in cloud services.
API stands for Application programming interface. API allows applications to communicate with each other. Cloud API enables end users to access cloud provider applications or services such as computing infrastructure, storage resources, monitoring tools. Cloud APIs provide a gateway or interface to interact with cloud services directly.
Q20. What are the categories of cloud APIs?
Cloud APIs are of three types namely – control APIs, Data APIs and APIs related to application functionality. Control APIs deal with infrastructure management on the cloud. Developers program these APIs mainly for integration of additional programs. Data APIs deal with flow of data from external elements to cloud service. APIs related to application deal with data present in the cloud and manages its flow for the end users.
Q21. Explain different forms of APIs.
There are four forms of cloud APIs.
-
PaaS APIs – also known as service level APIs, provide back end services and architecture for cloud environment. Facilitate integration with databases, portals and messaging systems
-
SaaS APIs – help to provide connectivity with a software suite such as ERP, CRM etc.
-
IaaS APIs – focus on providing storage and computing resources. Instant provisioning of
cloud resource is one such use case
-
Cross Platform APIs – Cross platform APIs enable cloud users to access resources not just
from their primary cloud provider but also from others
Q22.What is Container as a service or CaaS?
CaaS is a cloud based service which allows developers and operations teams to upload, organize, scale and manage containers using a virtual, container based environment. Containers as a service encompasses an infrastructure which include cloud machines and network routing machines. CaaS helps to streamline and manage the development of containers within a software defined infrastructure. It is a subset of IaaS wherein the main resource is container based instead of a virtual machine or bare metal hardware to support the IaaS on the cloud.

Q23. What is another name for ‘Serverless’ computing?
FaaS – Function as a service
Q24. Name some of the most popular open source databases on cloud computing.
MongoDB, CouchDB, LuchidDB
Q25. What is Openstack in cloud computing?
OpenStack is open standard and free platform for cloud computing. It is deployed mostly as IaaS in both private and public clouds where various virtual servers and other resources are available for end users. It helps to deploy interoperable cloud services like virtual machines, book more storage space, restart or re-image servers, read and write files to storage, create cloud computing
applications etc. This helps to avoid vendor lock in, enable easy horizontal scaling of services. The software displays multi-vendor hardware and network resources in cloud.

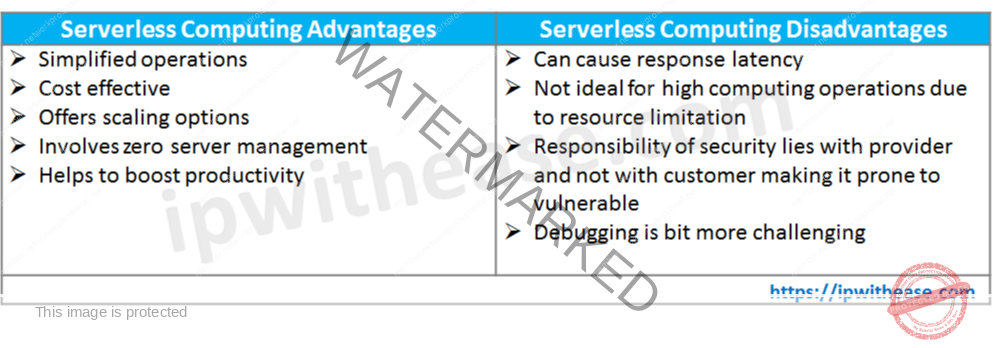
Q26. What are the advantages and disadvantages of serverless computing?
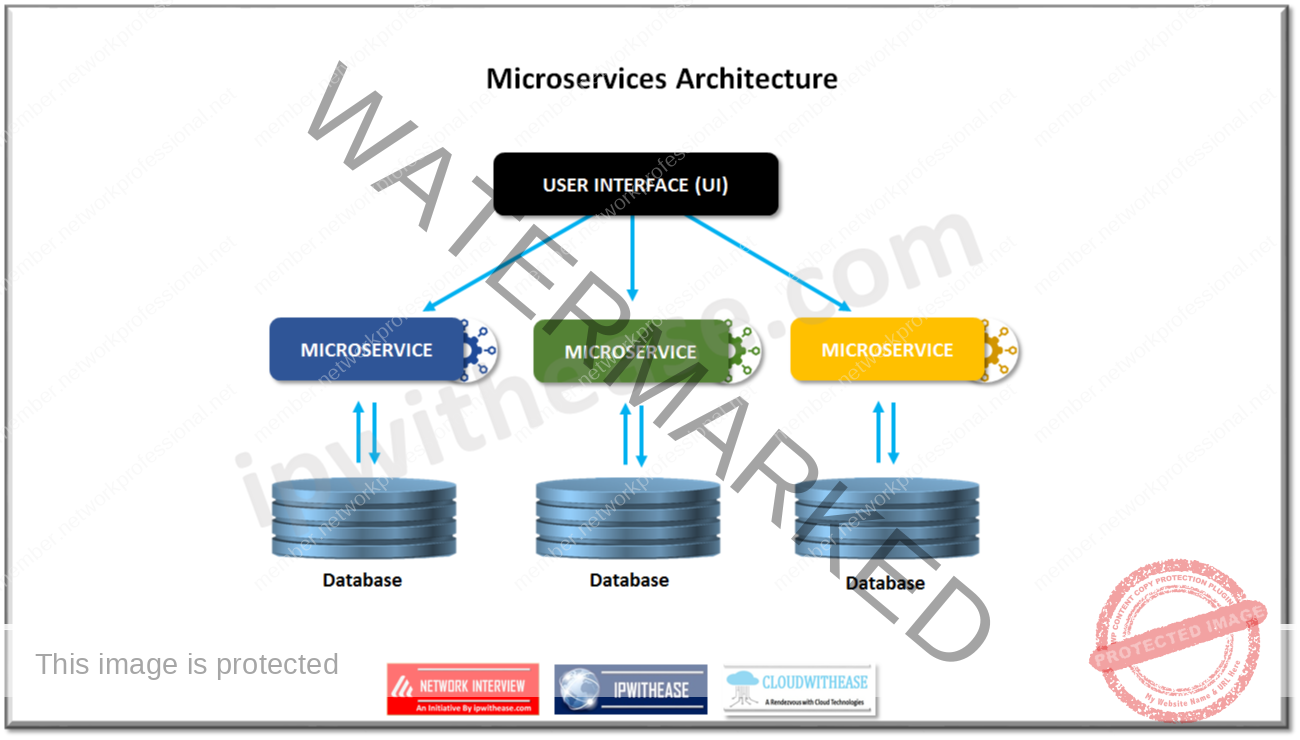
Q27. Explain the term ‘Microservices’.
Microservices is an architectural approach towards software development where software is composed of small independent services which communicate over well-defined APIs. These services are owned by self-contained teams. Each component service in microservice architecture can be developed, deployed, operated and scaled without affecting the functionality of other services. Services do not need to share any of their code or implementation with other services and all communication is handled by APIs only.
Q28. Elaborate difference between Monolithic and Microservices architecture.


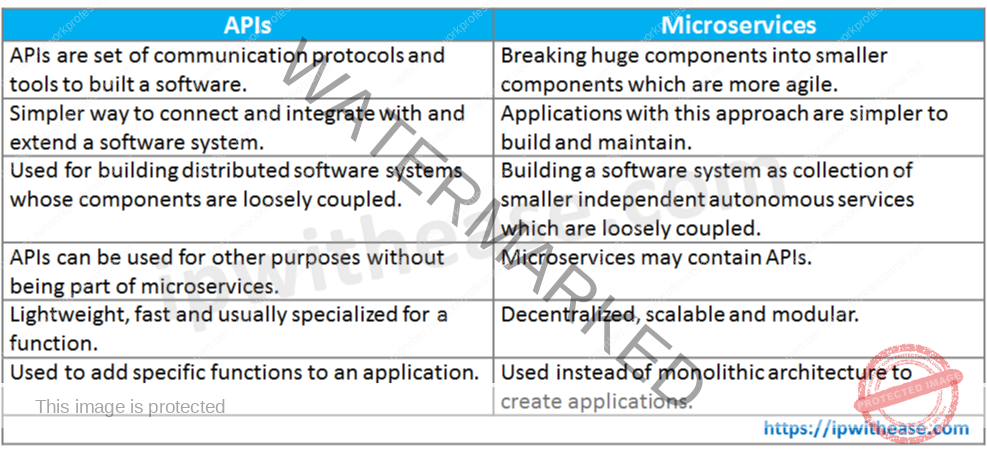
Q29. Elaborate difference between API and Microservices.
Q30. What do you understand about rate limiting and its usage?
Rate limiting is used to ensure the fair usage of APIs based services and other web services and resources by customers. It regulates the number of times a user can request a particular API based service in a given time frame. When thousands of users share a service, rate limiting helps to ensure the system to be available to all its clients. Rate limiting also protects a system from Denial of service attack wherein a malicious user might initiate a huge number of service requests in a short period which could lead to exhaustion of resources. This would mean the system becoming inaccessible to legitimate users. Limits on social media messaging is a typical example of such scenario.
Q31. Differentiate between cloud data replication and traditional data replication.

Q32. Name five cloud data replication tools.
Hevo data, Carbonite, AWS migration service, Veeam backup and replication, NaKivo
Q33. How resource replication works in cloud computing ? Explain
Data replication is the process of creation of clones of data and storing them in various locations. When we store data in multiple locations resource availability is improved and at the same time resiliency is also increased. Virtualization technology is used to implement the resource replication mechanism to replicate cloud based IT resources.

Q34. Describe in detail about cloud monitoring usage.
Cloud usage monitor is a lightweight and autonomous software program responsible for collection and processing IT resources usage data. Cloud usage monitor may have different formats depending on type of usage metrics are designed to collect and the manner in which usage data needs to be
collected. Agent based implementation formats exist – Monitoring agent – is an intermediary, event driven program which exists as a service agent and resides along existing communication paths to transparently monitor and analyse data flows majority used to measure network traffic and message metrics.
Resource agent – is a processing module which collects usage data by having event driven interactions with specialized resource software. This is used to monitor usage metrics based on pre- defined, observable events at resource software level like initiating, suspension, resumption and scaling vertically.
Polling agent is a processing module which collects cloud service usage data by polling IT resources. Typically used to monitor uptime and downtime statistics.
Q35. What is cloud VPN?
Cloud VPN is a new type of virtual private network which allows users to securely access organization data over cloud via a globally available connection. Cloud VPNs are also referred to as VPN as a service (VNaaS) or hosted VPNs. Cloud VPNs offer secure, efficient and remote alternative to traditional VPN services. Data is encrypted during the transmission over cloud.
Q36. Differentiate between Application load balancer (ALB), Network load balancer (NLB) and Elastic load balancer (ELB).

Q37. How is the virtual cloud isolated in public cloud ? Explain.
A virtual private cloud (VPC) is a secure, isolated private cloud hosted within a public cloud. VPN customers can run code, store data, host websites, and do all activities that they can perform in ordinary private cloud but this private cloud is hosted remotely by a public cloud provider. VPC isolates computing resources from other computing resources available on public cloud using some key technologies as under.
-
Subnets – subnet is a range of IP addresses within a network reserved so that they are not available for everyone within the network and divides the network for private usage. In VPC these private IP addresses are not accessible via public internet.
-
VLAN – VLAN is used to partition network on layer 2
VPN – uses encryption and creates a private network over a public network. A VPC will have a dedicated subnet and VLAN to prevent anyone on public cloud from accessing computing resources within VPC.
Q38. What is Elastic Compute cloud (EC2)?
Elastic compute cloud is on demand computing service on AWS cloud platform. It includes all services a computing device has to offer along with flexibility of virtual environment. It allows user to configure their instance as per their requirements such as RAM allocation, storage as per need of current task etc. EC2 provides virtual machines on rent and provide support for wide range of operating systems to choose from Amazon linux, Windows server, Ubantu server, SUSE linux, Red hat linux and so on.
Q39. What is the function of Cloudformation?
AWS Cloudformation provides developers and system administrators a simple way to create, maintain, provision, and update collections of AWS resources in a reliable manner. It uses templates written in JASON or YAML format to describe collection of AWS resources. We can use template to have similar copies of same stack across AWS regions. Post deployment resources can be modified or updated as required.
Q40. What is the function of Amazon Cloudwatch?
Amazon cloudwatch is a set of services that ingests, interprets, and responds to runtime metrics, logs, and events. It collects metrics from many AWS services automatically such as Amazon EC2, ELB etc . Cloudwatch comprises of three services: the leading cloudwatch service, Amazon cloudwatch logs and Amazon cloudwatch events.
Q41. How does Google cloud provide protection against Distributed denial of services (DDoS) attacks?
Google cloud Armor is Google DDoS protection service and web application firewall also. Cloud Armor adaptive protection is a machine learning capability to protect applications and services from layer 7 DDoS attacks. Adaptive protection provides early alerts on anomalous requests on a per backend service basis, dynamically generates signatures to describe potential attacks, suggest customer WAF rule to block the offending traffic.
Q42. Provide comparison between Amazon Aurora and Amazon RDS.

Q43. How is vertical scaling supported in AWS?
Vertical scaling in AWS supported using AWS Ops Automator which adjusts capacity to maintain steady, predictable performance at lowest possible cost. Vertical scaling is achieved by adding more RAM and processor power to existing virtual machines. AWS provides instances up to 488 GB RAM or 128 virtual cores. The vertical scaling requires decoupling of tiers in the application. These tiers will be distributed and handled by web servers. The instances can be resized by restarting an existing instance with new size or by replacing the current instance with new resize instance.
Q44. Define elastic IP?
An elastic IP is a static IP address designed for dynamic cloud computing. An elastic IP address is associated with AWS cloud account and can be used until it is released. An elastic IP address is a public IPV4 address which is reachable from the Internet. Elastic IP address can be associated to an instance to enable communication with internet. If an instance goes down in AWS, elastic IP maintains your IP address and communication with your AWS account.
Q45. What is Google Bigquery used for ?
Google Bigquery is a fully managed, massive scale, low cost enterprise data warehousing solution on google compute engine (Storage and network infrastructure). It is fully managed, serverless, cloud data warehouse. It allows business users to derive insights faster, it is extremely fast and lets you write queries using SQL like syntax as well, it has machine learning features and business intelligence.
Q46. How many storage accounts are supported by Azure subscription?
Azure subscription supports up to 100 storage accounts.
Q47. Compare Azure storage account services.
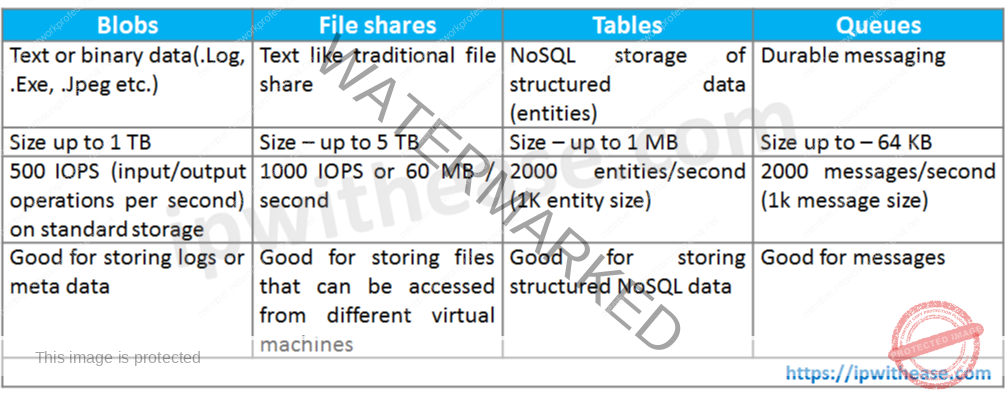
Q48. What are the common security risks in cloud computing?
Some of the common security risks in cloud are:
-
Data loss – data loss is a shared cloud risk. Data stored on cloud can be either hacked, leaked, deleted, corrupted, or misused by a malicious user or application
-
Hacked interfaces and insecure APIs – APIs are interfaces which let us connect to cloud provider services, hackers can attack them as they are in the public domain.
-
Data breach is a very high concern on cloud environments where data is leaked due to lack or ignorance of associates or due to poorly designed security controls over cloud
-
Denial of service attacks – cloud services can be targeted by flooding systems with numerous requests leading to systems crash
-
Account hijacking is a serious concern on cloud, where in malicious users or hacker can steal cloud account credentials to gain access to personal information
Q49.List down the advantages of using Azure content delivery network.
Azure content delivery network or CDN is a remote server cluster. It helps in delivering content at geographically distinct locations to users without much hassles and offers faster delivery over networks. Some of the benefits of using Azure content delivery network are as under:
-
Faster performance and better user experience
-
No requirement to add hardware/ software resources only configuration to setup CDN
features
-
Decrease in load on actual servers as data is sent via edge servers
-
Robust delivery system with minimal maintenance requirement
-
Easy to configure
Q50. Describe Amazon machine image.
An Amazon machine image is a special type of virtual machine which runs on cloud. It is a master image which contains information required to launch instances in the cloud. The virtual servers are known as EC2 in AWS environment. An AMI serves as a basic deployment unit for services given by EC2. Each AMI is configured with a template for root volume needed for a specific type of instance.
- General Interview Preparation
- Network Phone Interview Questions
- Network F2F Interview Question
- Company Interview Questions
- Troubleshooting Questions
- How to Own an Interview
- Wireless Interview Questions
- Security Interview Questions
- Technical Scenario Interview Tips
- Company Projects for Interviews
- SDWAN Interview Questions
- Cyber Interview Questions
- Network Automation Interview Questions
- VPN Top 100 Interview Questions and Answers
- 50 Cloud Engineer Interview Questions and Answers
- ASA Firewall Interview Questions and Answers
- CEH Interview Questions and Answers
- Cisco FTD Interview Questions and Answers
- Wireless Interview Questions & Answers