EIGRP Route-Map Filtering
EIGRP supports filtering with access-lists and prefix-lists but you can also use route-maps. In this lesson I’ll show you how to use a route-map to filter in- and outbound route advertisements. We will use the following topology for this:
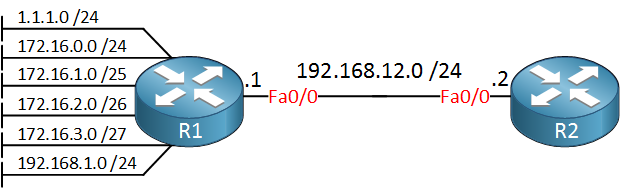
We only need two routers for this demonstration. R1 has some networks that it will advertise to R2 through EIGRP. Here’s what the routing table of R2 looks like:
R2#show ip route eigrp
1.0.0.0/24 is subnetted, 1 subnets
D 1.1.1.0 [90/409600] via 192.168.12.1, 00:00:45, FastEthernet0/0
172.16.0.0/16 is variably subnetted, 4 subnets, 4 masks
D 172.16.0.0/24 [90/409600] via 192.168.12.1, 00:00:14, FastEthernet0/0
D 172.16.1.0/25 [90/409600] via 192.168.12.1, 00:00:08, FastEthernet0/0
D 172.16.2.0/26 [90/409600] via 192.168.12.1, 00:00:14, FastEthernet0/0
D 172.16.3.0/27 [90/409600] via 192.168.12.1, 00:00:13, FastEthernet0/0
D 192.168.1.0/24 [90/409600] via 192.168.12.1, 00:00:13, FastEthernet0/0Above you see that R2 has learned all networks behind R1. Let’s start with something simple…let’s say we want to configure R1 so that 192.168.1.0 /24 won’t be advertised to R2. Here’s how we do this:
R1(config)#router eigrp 1
R1(config-router)#distribute-list ?
<1-199> IP access list number
<1300-2699> IP expanded access list number
WORD Access-list name
gateway Filtering incoming updates based on gateway
prefix Filter prefixes in routing updates
route-map Filter prefixes based on the route-mapWe have to use the distribute-list command under the EIGRP process but as you can see it supports a route-map. Let’s use that and give it a name:
R1(config-router)#distribute-list route-map FILTER_OUT ?
in Filter incoming routing updates
out Filter outgoing routing updatesI’ll call my route-map “FILTER_OUT” and we will choose outgoing updates:
R1(config-router)#distribute-list route-map FILTER_OUT outNow we can create the route-map:
R1(config)#route-map FILTER_OUT ?
<0-65535> Sequence to insert to/delete from existing route-map entry
deny Route map denies set operations
permit Route map permits set operations
<cr>We will start with a deny statement:
R1(config)#route-map FILTER_OUT deny 10The route-map will require a match statement. There are a lot of things you can select for the match statement:
R1(config-route-map)#match ?
as-path Match BGP AS path list
clns CLNS information
community Match BGP community list
extcommunity Match BGP/VPN extended community list
interface Match first hop interface of route
ip IP specific information
ipv6 IPv6 specific information
length Packet length
local-preference Local preference for route
metric Match metric of route
mpls-label Match routes which have MPLS labels
nlri BGP NLRI type
policy-list Match IP policy list
route-type Match route-type of route
source-protocol Match source-protocol of route
tag Match tag of routeNot all of these options are possible when you use the route-map for filtering. Let’s start with a simple example, let’s look at the IP options:
R1(config-route-map)#match ip address ?
<1-199> IP access-list number
<1300-2699> IP access-list number (expanded range)
WORD IP access-list name
prefix-list Match entries of prefix-lists
<cr>Here we can use an access-list or prefix-list. Let’s try the access-list:
R1(config-route-map)#match ip address NET_192Don’t forget to create the actual access-list:
R1(config)#ip access-list standard NET_192
R1(config-std-nacl)#permit 192.168.1.0 0.0.0.255The route-map is almost complete. We have a deny statement that matches everything in our access-list. There’s one problem though, our route-map doesn’t have any permit statements. If we don’t add one then everything will be blocked. Let’s add it:
R1(config)#route-map FILTER_OUT permit 20
R1(config-route-map)#exitThis permit statement doesn’t require any matches. Let me show you an overview of our configuration so far:
R1#show running-config | section eigrp
router eigrp 1
network 0.0.0.0
distribute-list route-map FILTER_OUT out FastEthernet0/0
no auto-summaryR1#show route-map
route-map FILTER_OUT, deny, sequence 10
Match clauses:
ip address (access-lists): NET_192
Set clauses:
Policy routing matches: 0 packets, 0 bytes
route-map FILTER_OUT, permit, sequence 20
Match clauses:
Set clauses:
Policy routing matches: 0 packets, 0 bytesAbove you can see that the route-map is attached to the distribute-list command in EIGRP. Our route-map will deny everything that matches our access-list while everything else is permitted. Let’s take a look at R2 to see if this works:
R2#show ip route eigrp
1.0.0.0/24 is subnetted, 1 subnets
D 1.1.1.0 [90/409600] via 192.168.12.1, 00:01:01, FastEthernet0/0
172.16.0.0/16 is variably subnetted, 4 subnets, 4 masks
D 172.16.0.0/24 [90/409600] via 192.168.12.1, 00:01:01, FastEthernet0/0
D 172.16.1.0/25 [90/409600] via 192.168.12.1, 00:01:01, FastEthernet0/0
D 172.16.2.0/26 [90/409600] via 192.168.12.1, 00:01:01, FastEthernet0/0
D 172.16.3.0/27 [90/409600] via 192.168.12.1, 00:01:01, FastEthernet0/0That’s looking good, everything is in the routing table except 192.168.1.0 /24. Now you might be thinking that this was a lot of work just to filter one network…
You are right, this was a lot of work. The power of using a route-map for filtering is that we can use multiple statements and use a mix of filtering techniques.
For example let’s say that we also want to deny all prefixes in the 172.16.0.0 /16 range that use a /26 subnet or smaller subnet. We can do this by creating a prefix-list and attaching it to our route-map:
R1(config)#route-map FILTER_OUT deny 20
R1(config-route-map)#match ip address prefix-list SMALL_PREFIXES
R1(config)#ip prefix-list SMALL_PREFIXES permit 172.16.0.0/16 ge 26
R1(config)#route-map FILTER_OUT permit 30Above I changed route-map entry 20 to a deny statement that checks for our prefix-list called “SMALL_PREFIXES”. The last permit statement (sequence number 30) doesn’t have any match statements and is required to permit all other route advertisements. Here’s what the complete route-map looks like:
R1#show route-map
route-map FILTER_OUT, deny, sequence 10
Match clauses:
ip address (access-lists): NET_192
Set clauses:
Policy routing matches: 0 packets, 0 bytes
route-map FILTER_OUT, deny, sequence 20
Match clauses:
ip address prefix-lists: SMALL_PREFIXES
Set clauses:
Policy routing matches: 0 packets, 0 bytes
route-map FILTER_OUT, permit, sequence 30
Match clauses:
Set clauses:
Policy routing matches: 0 packets, 0 bytesOur first sequence number (10) is used to filter with an access-list, the second one (20) uses our prefix-list and the last one (30) permits everything else. Let’s check the result of R2:
R2#show ip route eigrp
1.0.0.0/24 is subnetted, 1 subnets
D 1.1.1.0 [90/409600] via 192.168.12.1, 00:38:18, FastEthernet0/0
172.16.0.0/16 is variably subnetted, 2 subnets, 2 masks
D 172.16.0.0/24 [90/409600] via 192.168.12.1, 00:38:18, FastEthernet0/0
D 172.16.1.0/25 [90/409600] via 192.168.12.1, 00:38:18, FastEthernet0/0Great, as you can see network 172.16.2.0 /26 and 172.16.3.0 /27 are gone fishing, they have been filtered because of the prefix-list. I think this example should give you a good idea about the flexibility of a route-map, you can use a variety of filtering techniques.
Let’s try one more thing…we can also use a route-map for inbound filtering. Let’s filter network 1.1.1.0 /24 on R2, to keep things interesting i’ll use the route-map in a different way:
R2(config)#ip access-list standard NET_1
R2(config-std-nacl)#deny 1.1.1.0 0.0.0.255
R2(config-std-nacl)#permit anyFirst we create an access-list. This access-list denies 1.1.1.0 /24 and permits everything else. Now we create the route-map:
R2(config)#route-map FILTER_IN permit 10
R2(config-route-map)#match ip address NET_1This route-map has only one permit statement. Everything that matches our access-list will be permitted. Let’s attach it to EIGRP:
R2(config)#router eigrp 1
R2(config-router)#distribute-list route-map FILTER_IN inNow we can check the routing table of R2:
R2#show ip route eigrp
172.16.0.0/16 is variably subnetted, 2 subnets, 2 masks
D 172.16.0.0/24 [90/409600] via 192.168.12.1, 00:56:08, FastEthernet0/0
D 172.16.1.0/25 [90/409600] via 192.168.12.1, 00:56:08, FastEthernet0/0Table of Content
Unit 2: EIGRP Neighbor Adjacency
Unit 4: EIGRP Advanced Features