MPLS Layer 3 VPN BGP AS Override
BGP has a simple loop prevention mechanism for external BGP. When you see your own AS number in the AS path, we do not accept the prefix. This mechanism is fine for Internet routing but there are some other scenarios where this might be an issue. Take a look at the following topology:
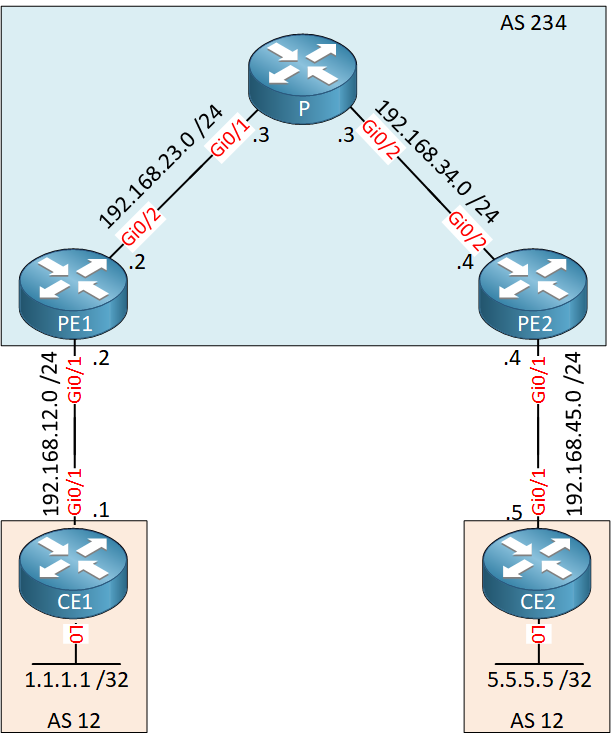
Above we have a small MPLS VPN network with two customer sites. The customer is using the same AS number (12) for both sites. When CE1 or CE2 receive an update from each other they will not accept it since their own AS number will be in the AS path.
Let’s find out if this is true. Here are the configurations of all routers:
- Configurations
- CE1
- PE1
- P
- PE2
- CE2
Here you will find the startup configurations of each device.
Let’s find out what is going on. First we’ll check if the PE routers have a VPN route for the prefixes from the CE routers:
PE1#show ip bgp vpnv4 all
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 1:1 (default for vrf CUSTOMER)
*> 1.1.1.1/32 192.168.12.1 0 0 12 i
*>i 5.5.5.5/32 4.4.4.4 0 100 0 12 iPE2#show ip bgp vpnv4 all
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 1:1 (default for vrf CUSTOMER)
*>i 1.1.1.1/32 2.2.2.2 0 100 0 12 i
*> 5.5.5.5/32 192.168.45.5 0 0 12 iThe PE routers have an entry for the loopback interfaces of the CE routers. Are they advertising these to the CE routers?
PE1#show ip bgp vpnv4 all neighbors 192.168.12.1 advertised-routes
BGP table version is 16, local router ID is 2.2.2.2
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 1:1 (default for vrf CUSTOMER)
*>i 5.5.5.5/32 4.4.4.4 0 100 0 12 i
Total number of prefixes 1 PE2#show ip bgp vpnv4 all neighbors 192.168.45.5 advertised-routes
BGP table version is 18, local router ID is 4.4.4.4
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 1:1 (default for vrf CUSTOMER)
*>i 1.1.1.1/32 2.2.2.2 0 100 0 12 i
Total number of prefixes 1The PE routers are advertising these to the CE routers. Let’s check the CE routers:
CE1#show ip bgp
Network Next Hop Metric LocPrf Weight Path
*> 1.1.1.1/32 0.0.0.0 0 32768 iCE2#show ip bgp
Network Next Hop Metric LocPrf Weight Path
*> 5.5.5.5/32 0.0.0.0 0 32768 iThere’s nothing there…they only have the prefix on their own loopback interface in the BGP table. Let’s enable a debug on CE1 to figure out why it’s not accepting anything from PE1:
CE1#debug ip bgp all updates
BGP updates debugging is on for all address familiesLet’s reset the neighbor adjacency:
CE1#clear ip bgp *Here’s what you will see:
CE1#
BGP(0): 192.168.12.2 rcv UPDATE about 5.5.5.5/32 -- DENIED due to: AS-PATH contains our own AS;No surprises here…CE1 is denying the update since it sees its own AS number in the AS path. If we want to keep the same AS number on CE1 and CE2 then there are two possible solutions for this issue:
- Allow-AS in: this can be configured on the CE routers which tells them to accept prefixes with their own AS number in the AS path.
- AS override: this can be configured on the PE routers, the AS number will be replaced with the AS number from the service provider.
This lesson is about AS override so that’s what we will do. Let’s configure the PE routers:
PE1(config)#router bgp 234
PE1(config-router)#address-family ipv4 vrf CUSTOMER
PE1(config-router-af)#neighbor 192.168.12.1 as-overridePE2(config)#router bgp 234
PE2(config-router)#address-family ipv4 vrf CUSTOMER
PE2(config-router-af)#neighbor 192.168.45.5 as-overrideTo speed things up, let’s clear the BGP neighbor adjacencies on the PE routers:
PE1 & PE2#clear ip bgp *Let’s take another look at the CE routers:
CE1#show ip bgp 5.5.5.5
BGP routing table entry for 5.5.5.5/32, version 7
Paths: (1 available, best #1, table default)
Not advertised to any peer
Refresh Epoch 1
234 234
192.168.12.2 from 192.168.12.2 (2.2.2.2)
Origin IGP, localpref 100, valid, external, best
rx pathid: 0, tx pathid: 0x0CE2#show ip bgp 1.1.1.1
BGP routing table entry for 1.1.1.1/32, version 7
Paths: (1 available, best #1, table default)
Not advertised to any peer
Refresh Epoch 1
234 234
192.168.45.4 from 192.168.45.4 (4.4.4.4)
Origin IGP, localpref 100, valid, external, best
rx pathid: 0, tx pathid: 0x0The CE routers have now learned each others prefixes. If you take a closer look, you can see that AS number 12 has been replaced with AS number 234.
One final check, let’s see if there is connectivity between 1.1.1.1 and 5.5.5.5:
CE1#ping 5.5.5.5 source loopback 0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 5.5.5.5, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 6/8/11 msExcellent this is working! Want to take a look at these configurations yourself?
- Configurations
- CE1
- PE1
- P
- PE2
- CE2
Here you will find the startup configurations of each device.
Conclusion
AS override is a simple technique to change the AS number of updates that you advertise to your external BGP neighbors. Another solution is allow AS in but this is configured on the CE routers. Since we are “overruling” the external BGP loop prevention mechanism you have to make sure that you have a loop-free topology.
In this scenario there are no issues since the CE routers are stubs, they only have one exit path. When your customer sites are multihomed or have a backdoor link then you need to use the BGP SoO (Site of Origin) community to ensure you have a loop free topology. This is something we’ll cover in another lesson.
Unit 1: Introduction to BGP
- Introduction to BGP
- Single/Dual (multi) homed connections
- eBGP (external BGP)
- eBGP Multi-Hop
- iBGP (internal BGP)
- How to read the BGP Table
- How to advertise networks in BGP
- iBGP Next Hop Self
- BGP Auto-summary
Unit 2: BGP Neighbor Adjacency
- BGP Neighbor Adjacency States
- BGP Messages
- Troubleshooting BGP Neighbor Adjacency
- Troubleshooting BGP Route Advertisement
Unit 3: BGP Attributes
- BGP Attributes and Path Selection
- BGP Weight Attribute
- BGP Local Preference
- BGP AS Path Prepending
- BGP Origin Code
- BGP MED (metric) Attribute
Unit 4: BGP Communities
Unit 5: BGP Filtering
- BGP Regular Expressions
- BGP Transit AS
- BGP IPv6 route filtering
- BGP AS Path Filter
- BGP Extended Access-List Filtering
Unit 6: Advanced BGP Features
- BGP Peer Groups
- BGP Route Reflector
- BGP Confederations
- BGP Synchronization
- BGP Backdoor Routes
- MP-BGP (multi-protocol BGP)
- BGP Private and Public AS Numbers
- BGP Remove Private AS Numbers
- BGP 4-byte AS numbers
- BGP Soft Reconfiguration
- BGP Route Refresh Capability
- BGP Allow AS in
- BGP AS Override
- BGP Aggregate AS-SET
- BGP Multipath eBGP and iBGP